Treading carefully in Share Enumeration
Wherever there's Windows in corporate environments, there are Windows File (SMB) Shares. More often than not, during Adversary Simulation exercises operators need to enumerate which shares exist on which hosts, who can read and/or write to them, what files they contain, etc. Scenarios often arise that may even involve enumerating shares to write to them, i.e. to coerce authentication upon browsing, etc. Naturally, due to the vast usage of this TTP (MITRE ID: T1135) amongst exercises and actual threat actors, there are plenty of methods to monitor such behaviors.
Monitoring enumeration attempts
In most corporate environments, shares are typically accessed at any given time by mulitple hosts, creating extensive amounts of logging. Effective monitoring against share enumeration attempts usually revolves around a given timeframe, which is usually small. By corellating Windows Security events and network traffic logs a small subset of rules could be as follows:
- Any host communicates with more than 10 hosts on port 445 in the last 5 minutes
- Any host successfully authenticates an account rapidly in the last 5 minutes
- Any host rapidly requests Service Tickets in the last 5 minutes
- ...
More detailed information can be found in this article by Splunk on the topic.
Fine-tuning the toolset
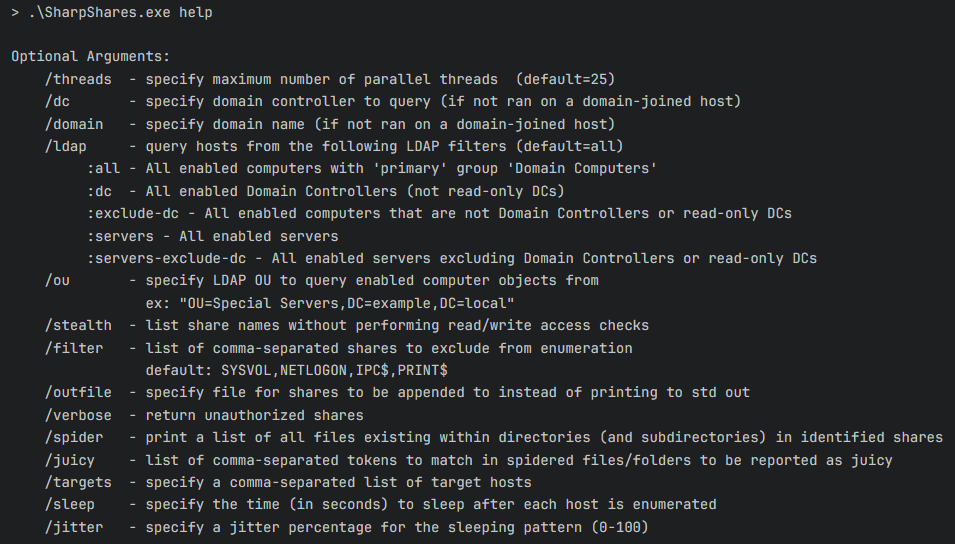
In order to evade such monitoring attempts, the Red Team at Hackcraft utilizes custom tooling that can be fine-tuned in terms of behavior to fly under the radar when such monitoring is in place. Regarding share enumeration specifically, an open-source tool was forked for this very reason, SharpShares.
Our fork adds the following list of features:
- Support for specifying a sleep/jitter combo, which is used to determine a sleep duration after each enumeration action it performs.
- Support for spidering files in shares, along with identification of interesting files based on a user provided keyword list.
- Support for specifying the target list in the command line instead of enumerating it from the Active Directory to allow for a minimal footprint.
Contributing
Our fork of SharpShares can be found on the Hackcraft Github. Contributions and additions to the project are always welcome. Have fun mining shares and thank you for reading! 🙂


